Class 19. The Hack and Dump in 2016
Why it's important to understand the thru line from "But her emails" to "Hunter Biden's laptop."
It feels a little Throwback Thursday to talk about the hack and dump of the Clinton/Democratic Congressional Campaign Committee/Democratic National Committee emails from 2016 — I mean, haven’t we had enough of, “But her emails”? We have, but it’s important to revisit this aspect of Russia’s election interference to understand the current moment, including the Hunter Biden Laptop scandal, the so-called “Twitter files,” and the whole clown show involving Representative Jim Jordan’s “weaponization of government” committee. The failure to understand how all of these pieces fit together is a huge vulnerability, since ultimately what is being exploited is the public’s naïveté and willingness to take the bait when it comes to manipulating their attention and perceptions.
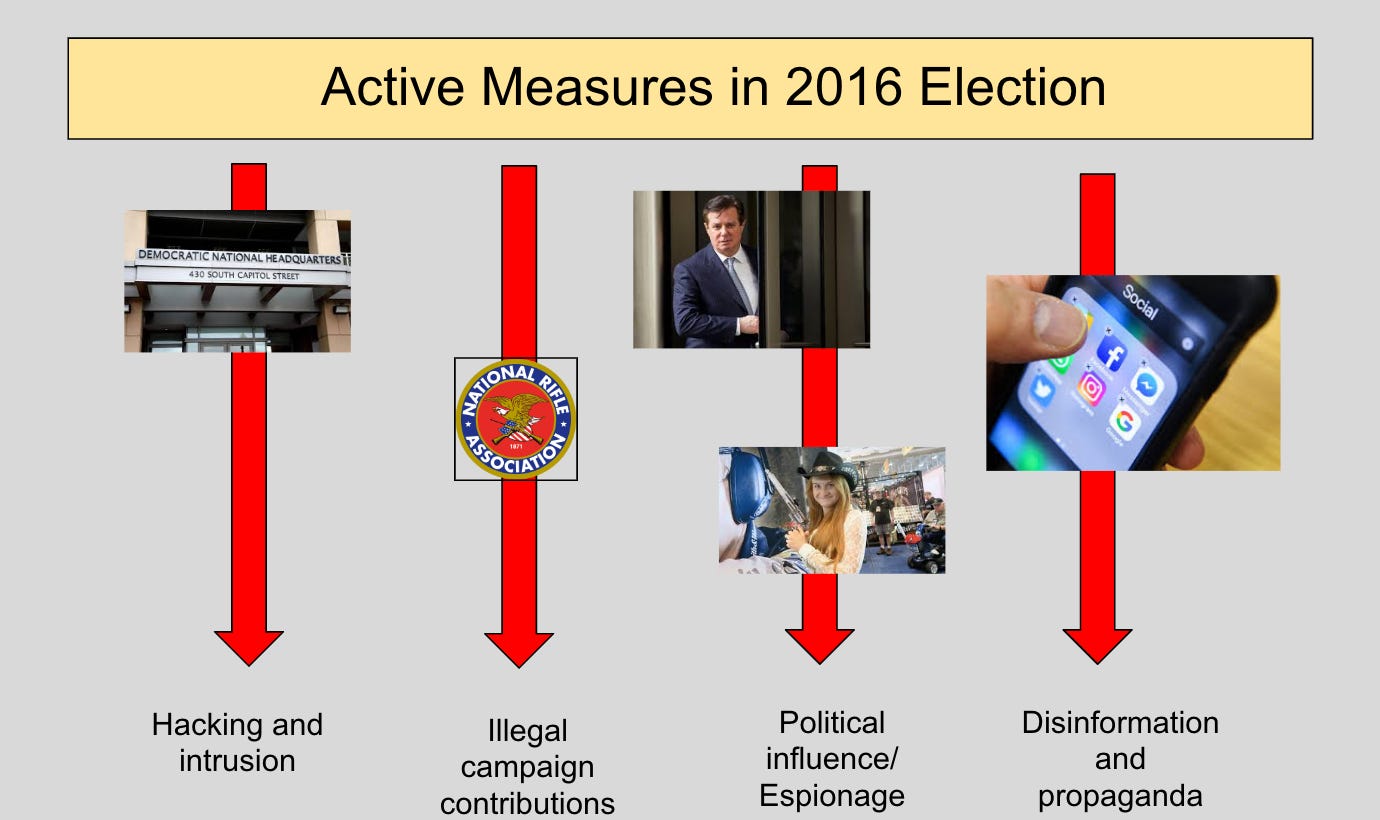
So let’s start by understanding the big picture. The hacking of emails was a part of a larger suite of active measures used in the 2016 presidential election. (If you’re just joining, Classes 5-7 give an overview of what “active measures” are and how they work.) In short, there was a lot of spaghetti being thrown at the wall, and looking at any of them only in isolation misses how extensive and pervasive the entire attempt to undermine our election actually was. Here is a little graphic that can help break down some of the separate threads:
As the diagram shows, in addition to the hacking, we saw the influx of Russian money into the election. For example, Russians tied to the Kremlin contributed money to the NRA, perhaps as an attempt to use the organization as a straw donor to Trump (the NRA contributed $30 million to Trump’s campaign, much more than it had to previous Republican candidates), and to Trump’s inaugural fund. (One political consultant was charged by the Justice Department just last year with trying to funnel Russian money into Trump’s 2016 campaign.) In another thread, we had individuals like Paul Manafort who were actively in contact with individuals connected to Russian intelligence, and spies like NRA darling Maria Butina, who was making the rounds with influential Republican figures. And finally, we have the main focus of this class, which involved the disinformation operation on social media.
You’ll note that I have separated the hack and dump operation from the social media disinformation operation, which is a key distinction. Many commentators discussing the 2016 election interference fail to distinguish between these two tactics even today. I remember feeling incredibly frustrated when, in early 2017, I wrote an op-ed for The Washington Post on why the social media disinformation campaign was so pernicious (it’s actually still my favorite piece I’ve written), and the editors wrote a headline that made it seem like I was talking about “Russian hacking.” These are two different things, and conflating them is not only inaccurate but prevents us from taking the appropriate steps to address them with different legal and policy tools.
In fact, if there is one takeaway from this entire post, it’s that it’s important to distinguish the term “disinformation” from “information operation.” Disinformation is often used as part of an information operation, but not all information operations necessarily use disinformation. Can we repeat that? Disinformation is often used as part of an information operation, but not all information operations necessarily use disinformation. Unfortunately, these concepts are typically used interchangeably, which has led to a significant amount of confusion and has allowed people like Jim Jordan and his ilk to mischaracterize the FBI’s good faith efforts to prevent something like the 2016 hack and dump from happening again — which means that 2024 may once again be open season.
I won’t get into too much detail on the mechanics of the 2016 hack, which according to the indictment filed by Special Counsel Robert S. Mueller III in 2018 was pretty straightforward. As it explains, the GRU, Russia’s military intelligence service, utilized some pretty basic spearphishing techniques to obtain passwords to the various networks. The GRU then stole documents related to the 2016 presidential election and strategically released them using intermediaries posing as sites unconnected to the Russian government, like Guccifer 2.0, DC Leaks, and Wikileaks. It’s not that complicated.
What’s more interesting than the what is the so what — why this particular operation was significant. I posit three main reasons.
The first is that, as we discussed in the conversation with former FBI Deputy Director Andrew McCabe last month, the hack and dump represented a departure from the traditional goals of cyber espionage. The second is that the operation illustrated a very successful use of reflexive control, a concept which we reviewed in a previous class but will look at again here. And finally, this same tactic appeared to be underway in the lead up to the 2020 election, which resulted in a series of events that would ultimately become the Hunter Biden Laptop/Twitter files scandal.
Let’s look at each of these in turn.