Framing Hunter Biden
Your quick reference guide for understanding the Hunter Biden Laptop scandal and meta-scandal. Buckle up.
If you’re like me, the phrase “Hunter Biden’s Laptop” provokes a peculiar physiological response: My eyes glaze over, I get sort of sleepy, and my mind starts looking for something practical to think about, like my week’s grocery list. The phrase has come to mean everything and nothing — the person uttering it probably can’t tell you exactly what they are alleging, only that it is very, very illegal. It kind of reminds me of “Whitewater” back in the 90s. Be honest Gen Xers, if someone were to ask you, right now, to explain Whitewater in three sentences, could you do it? I think most people couldn’t; I know for me the phrase is really just a lot of random word association. e.g., Whitewater/Clintons/land deal/suicide (remember Vince Foster??) that is shorthand for some vague criminality no one can articulate. And that’s the point.
Unfortunately, with the Republicans in control of the House — and in particular the capitulation of power to the extreme MAGA contingent — we can expect there to be endless hearings centered around Hunter Biden’s Laptop. Which means it behooves us to understand what, exactly, it is really about. I’ll be diving into conspiracy theories later in my online course, but for now, the question is: Is Hunter Biden’s Laptop a conspiracy theory, or evidence of a real conspiracy? To unpack this, I use a basic three-part formula that psychologists who study conspiracy theories suggest for disentangling truth from fiction, one that activates the rational, analytical side, rather than the lizard, fight-or-flight side, of the brain:
What is the evidence for your claim?
What is the source of evidence for this claim?
What is the reasoning that links your evidence back to the claim?
Of course, before we can answer these three questions we need to articulate what the claim(s) actually is (are) — which is one of the main challenges. (As with the Whitewater example, the purpose is to keep this part a little hazy and obscure.) I found the best deep dive for getting to the bottom of this question a New York magazine Intelligencer piece by Andrew Rice and Olivia Nuzzi, which is worth the read. (Full disclosure: I am a huge fan of Nuzzi’s work, including her unparalleled coverage of the most important political event of 2020, the Four Seasons Total Landscaping Press Conference.) It’s a long piece, and one that starts off pretty straightforwardly but ends up going down some crazy rabbit holes. It’s best read with a drink.
In any event, onwards. Let’s get to our analysis.
What is the Claim?
The Hunter Biden Laptop scandal is best described as two scandals: The primary scandal and then the scandal about the scandal. For ease of understanding, I will refer to them as Scandal 1 and Scandal 2. Further, there are two claims in Scandal 1, which I will refer to as Claim 1a and Claim 1b. They are as follows:
Claim 1a:
The first claim is that Joe Biden’s efforts (while he was Vice President) to pressure the Ukraine government to fire the prosecutor who was investigating Burisma, a Ukrainian company, was influenced by Hunter Biden, who was on Burisma’s board from 2014-2019. (There is also a subtext claim that Hunter was himself under investigation and seeking to save his job.)
Claim 1b:
The second claim is that Joe Biden financially profited from Hunter Biden’s deals in China.
If Claim 1a sounds familiar, it’s because it’s an extension of the claim that was underlying Trump’s “perfect phone call” with Ukrainian President Volodymyr Zelinsky in 2019, and which ultimately led to Trump’s first impeachment. And if Claim 1b doesn’t sound super familiar, it’s largely because it was eclipsed by the circumstances surrounding Scandal 2:
Claim 2
The FBI pressured and/or ordered Twitter and other social media platforms to suppress the Hunter Biden Laptop story published by the New York Post in October 2020.
OK. Now that we have distilled the specific claims being made about Hunter Biden’s Laptop, let’s turn to the evidence.
What Is the Evidence for the Claims?
In reviewing the evidence for the claims cited above — at least for Claims 1a and 1b — I want to be clear that I am looking at evidence connected to the laptop, since the relevance of the laptop is what is in question. (Much of the impeachment-related claims that were made about Joe Biden and Burisma, for example, were independently debunked.) But the question for our purposes are what, exactly, the laptop supposedly revealed about these allegations.
Evidence 1a
The main evidence for Claim 1a is a “smoking gun” email sent in 2015 from Vadym Pozharski, an adviser to Burisma’s board, to Hunter, which says the following: “Dear Hunter, thank you for inviting me to DC and giving an opportunity to meet your father and spent [sic] some time together. It’s realty [sic] an honor and pleasure.”
The other piece of evidence, cited by the New York Post, is a purported email (more on why this is “purported” below) with the subject line “Urgent Issue” sent by Pozharski to Hunter in 2014, which states, “We urgently need your advice on how you could use your influence to convey amessage / signal, etc .to stop what we consider to be politically motivated actions bearing in mind the following…”
Evidence 1b
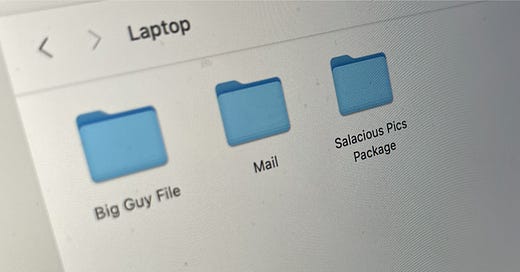
The primary evidence for Biden profiting from Hunter’s China deals is a 2017 email with the subject line “Expectations.” The email outlines a proposed corporate structure for a business venture in which Hunter would receive 20% and 10% would be “held by H for the big guy.”
The second piece of evidence is an email two months later from Hunter Biden for a separate business deal with the same Chinese energy magnate in which he discusses that the terms of that deal had been changed to a “much more lucrative arrangement” that would be “so much more interesting to me and my family.”
Evidence 2
The evidence for Claim 2 mainly comes from a 49-part (yes, 49) Twitter thread by Michael Schellenberger, Part 7 of the so-called Twitter files. The “Twitter files,” in case you are unfamiliar (because your eyes glazed over and you started thinking about your grocery list) are exposes written by Elon Musk’s hand-picked journalists to review Twitter’s internal decisions leading up to the 2020 election.

This claim relies on the following pieces of evidence:
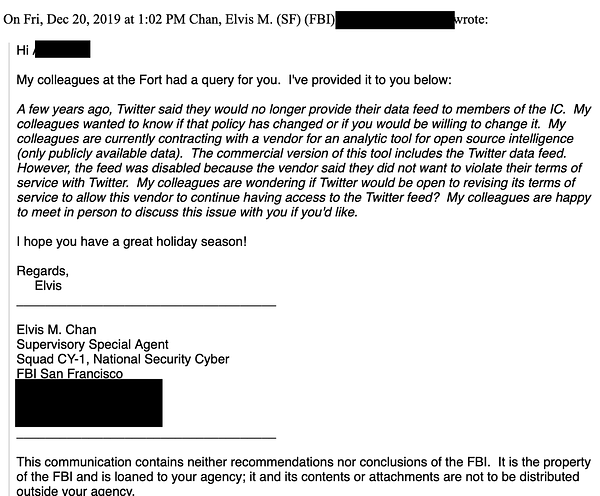
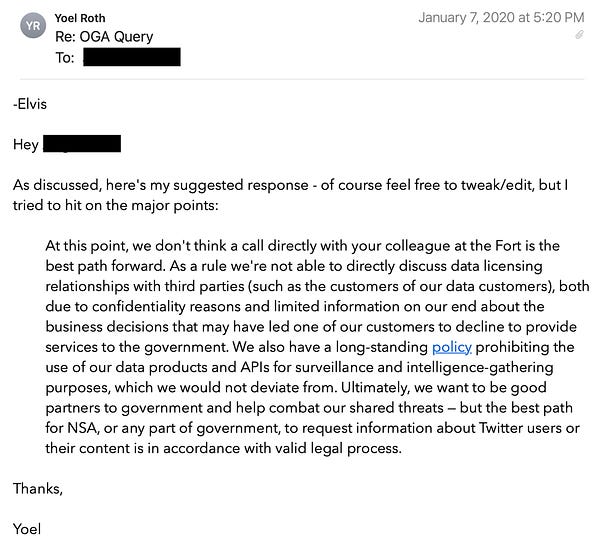
Throughout 2020, the FBI maintained contact with Twitter’s former Head of Trust and Safety, Yoel Roth, and with Mark Zuckerberg, advising them to be on “high alert” for a potential hack and leak operation by Russia right before the presidential election.
The FBI conducted an Aspen Institute “tabletop exercise” with social media platforms in September 2020, with the scenario based on a hack and dump involving Hunter Biden.
In mid-September 2020, the FBI set up an encrypted messaging channel for Roth and Twitter employees to communicate with the intelligence community.
Twitter employs a number of former FBI agents, and in particular had hired James Baker, former General Counsel of the FBI, as its Deputy General Counsel.
The FBI gave a classified briefing to James Baker in September 2020 without other Twitter officials present.
The evening before the New York Post published its October 2020 Hunter Biden story, the FBI sent 10 documents to Roth.
Are you still with me? Great — let’s turn to the sources of the evidence.
What is the Source of the Evidence?
The source of Claim 1a and b is the laptop, and the many problems surrounding the laptop is what leads to Claim 2.
Source for Claims 1a and 1b
Hoo boy. I may need to diagram the chain of custody of the laptop emails, but will try to give a quick synopsis here (the Rice and Nuzzi article does a really good job of laying out the chronology):
In April 2019, a man dropped off three laptops at computer repair shop in Delaware owned by a man named John Paul Mac Isaac. The receipt is signed by “Hunter Biden,” though Mac Isaac cannot positively identify the man who left the laptop because he is legally blind. The person who dropped off the laptops never picked them up. One laptop was dead, one was rebooted, and the third required more work. While repairing the third laptop Mac Isaac claims he came across what he believed was evidence of corruption. He made a copy of the hard drive for himself and called the FBI. The FBI issued a subpoena and collected the laptop. After several months passed and Mac Isaac did not hear back from the FBI, he reached out to Jim Jordan and Lindsey Graham, but they didn’t respond. So he finally reached out to Rudy Giuliani. Guiliani’s lawyer, Robert Costello, responded immediately.
From there, it appears that several copies of the hard drive were made. One was sent to Costello. Costello shared it with Giuliani, who shared it with Steve Bannon. Bannon contacted Emma Jo-Morris, Deputy Political Editor of the New York Post, who made a copy of some files to a thumb drive. Eventually, Giuliani and Bannon provided her with a copy of the entire drive. (Later, after the New York Post story was published, Bannon’s War Room co-host, Jack Maxey, sent copies of the hard drive to Republicans in Congress, various news outlets, and a computer analyst in Switzerland.) As far as I can tell, there are now lots of copies floating around. In short, the chain of custody issue creates some problems for news outlets trying to verify the authenticity of all of the hard drive’s contents, as Rice and Nuzzi note:
The many alterations made the laptop all but impossible to trust. ‘The forensic quality of this thing is garbage,’ says Johns Hopkins computer-science professor Matthew Green, a cryptography expert who examined the drive for the Washington Post. He told the paper that it was like a crime scene that previous detectives had left strewn with burger wrappers.
In fact, even Mac Isaac, the origin of the copied hard drive, has indicated that some of the supposed contents of the laptop which have leaked out over the last two years are not familiar to him. (As of the publication of the New York magazine article, Hunter Biden had not conceded that he was the individual who dropped off the laptop(s) and his legal team is still reviewing the contents of the hard drive, a copy of which they have obtained from a government source.)
Still, at this point several news outlets have authenticated many of the emails and have based reporting on the contents of the laptop, including Hunter Biden’s China deals. There is some question, however, about the authenticity of the “Urgent Issue” email that is part of the evidence for Claim 1b. In particular, this email is presented as a pdf, the metadata of which reveals that it was created several months after the email it purportedly represents.
Source for Claim 2
In contrast to Claim 1a and 1b, the source of Claim 2 are internal files at Twitter. The authenticity of these documents aren’t in question, but because they have been filtered through specific journalists with whom Musk has chosen to share this information, they may be selective and incomplete. In particular, Shellenberger’s Twitter thread presents screenshots of his supporting documents — many of them cropped — making it difficult to see the full context for the underlying communications. Further, to my knowledge Musk has not shared these internal documents with other journalists to conduct their own review.
What is the Reasoning that Links the Evidence to the Claim?
Key to making Scandal 1 politically relevant is establishing a (not always clearly articulated) connection between the emails found on the laptop and Joe Biden. After all, even if these emails were evidence of illegality on their face or criminality (and they don’t appear to be, to me), who cares? Hunter Biden is just a citizen, not a government official. The missing link that bumps this up to Congressional Inquiry Status is a connection to Joe Biden.
Scandal 2 requires demonstrating that top of mind for the FBI in 2020 was in preventing damaging information about Hunter Biden from coming to light, in an effort to ensure that Joe Biden would be elected. (Keep in mind that Trump was the president — and his own appointee in charge of the Justice Department — while the FBI was ostensibly engaged in this effort.)
Both scandals fail in the logical reasoning needed to reach these conclusions.
The Reasoning Behind Claims 1a and 1b
If you look at the evidence cited against their respective claims, it’s easy to see that there are many logical leaps and inferences that need to be made in order to get from one to the other. For example, Claim 1a rests on an assumption/inference that Joe Biden did in fact meet with Vadym Pozharski (which he denies and for which there is no affirmative evidence). It also rests on the assumption that Hunter Biden used his position at Burisma to influence Biden’s foreign policy actions. There is also an implication that Hunter’s activities while on the board may have been the subject of investigation. (In fact, Ukraine’s investigation into Burisma involved activities that predated Hunter Biden’s ascension to the board.) In fact, as noted previously, Claim 1a largely builds on the narrative which was underlying Trump’s quid-pro-quo with Ukraine, and this narrative has already been debunked by independent fact checkers — meaning that the intermediate steps to get from the evidence to the claim doesn’t exist. (Even Steve Bannon thought the Ukraine narrative had outlived its expiration date.)
Similarly, Claim 1b first rests on the assumption that “the big guy” refers to Joe Biden, that the proposed business deal came to fruition and that Joe Biden was in the loop and got some kind of cut. (Rice and Nuzzi note that that the proposed business venture actually fell through.) The other China deal from which Hunter Biden and his uncle, James Biden, did make a lot of money have been investigated by numerous outlets, including the Washington Post and CNN, both of which found no evidence that Joe Biden knew of or personally benefited from Hunter’s overseas ventures.
(But Wait…Isn’t Hunter Biden Under Federal Investigation?)
Yes, he is. Ironically, the investigation reportedly began as a tax inquiry under the Obama administration and took on a broadened scope in 2018 to investigate whether Hunter Biden failed to report and pay taxes on his foreign income, as well as whether he had violated the Foreign Agent Registration Act or money laundering laws. The investigation also involves whether Hunter Biden lied on a gun purchase form. But that investigation predates the laptop and is not directly relevant to Claims 1a and 1b involving Joe Biden. (Note that this investigation is overseen by the U.S. Attorney in Delaware and Trump appointee David Weiss, who has been allowed to remain in his position as the case proceeds.)
The Reasoning Behind Claim 2
The main thrust of Schellenberger’s Twitter files thread is that the FBI was purposely grooming social media platforms to be wary of any information specifically involving Hunter Biden, and subsequently pressured them to suppress the laptop story, despite knowing the contents to be authentic (presumably since it had the laptop since 2019).


This overarching narrative ignores three key factors. First, the backdrop of the FBI’s communications with social media platforms in 2020 was to avoid a repeat of Russia’s successful hack and dump of DNC emails in 2016 — an operation involving emails that, while authentic, were released by a foreign adversary in an effort to hijack the news cycle and distract from damaging information about Donald Trump. Second, the source of the laptop’s contents to the New York Post, Rudy Giuliani, was under an active counterintelligence investigation as a potential target of Russian intelligence at the time. Finally, it was reported in early 2020 that Burisma emails had been hacked by Russia, making a repeat of 2016 using hacked emails involving Hunter Biden a predictable hypothetical to use for the tabletop exercise. Philip Bump of the Washington Post offers an excellent historical timeline here.
But Schellenberger’s interpretation of various pieces of evidence are themselves misleading or outright false. For example, Schellenberger uses Twitter’s “pushback” against the FBI’s query about the origins of certain accounts on Twitter as proof that the FBI was trying to steamroll the social media platform into seeing ghosts. However, the pushback makes clear that Twitter was making independent judgments about content on its platform and not afraid to disagree with the FBI — not exactly a victim of a pressure campaign.

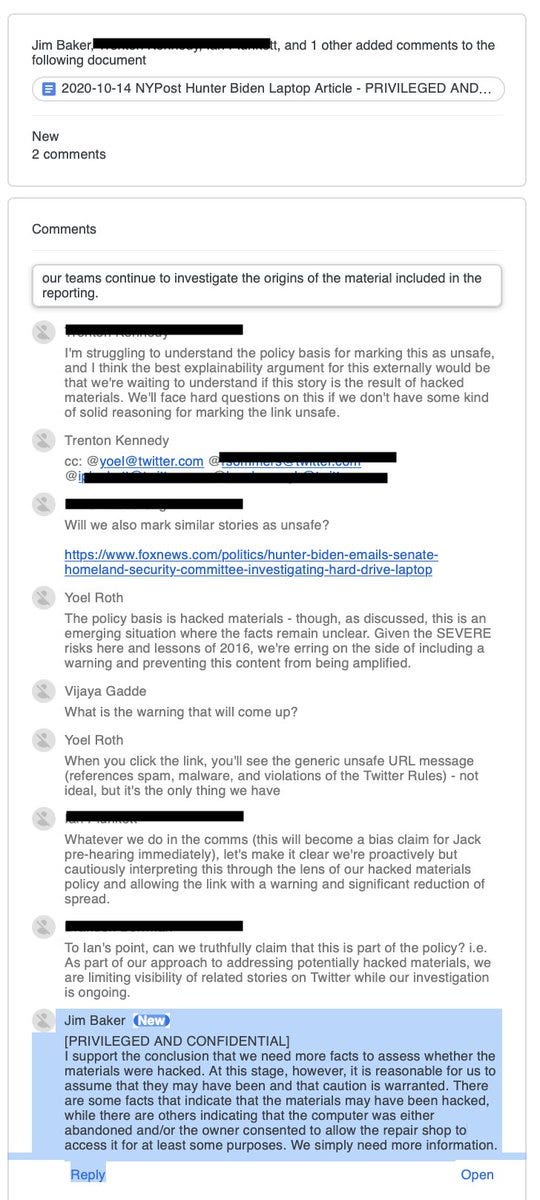
In another example, Schellenberger claims that Twitter’s Deputy General Counsel Jim Baker “repeatedly insist(ed) that the Hunter Biden materials were either faked, hacked, or both….” But if you look closely at the screenshotted material, Baker in fact says that he can’t be sure and that they “simply need more information.”


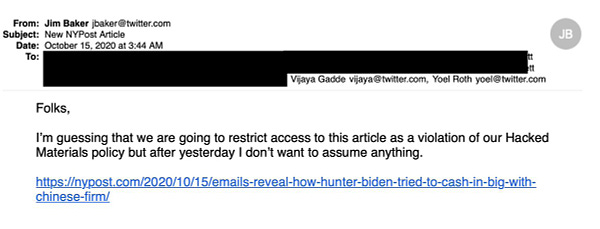
Other examples of the logical inconsistencies between what the Twitter Files Part 7 claim to have found and what the evidence reveals can be found here.
Finally, Schellenger makes much of the fact that certain former FBI employees employed at Twitter, like Baker and Dawn Burton, had previously worked with former FBI James Comey — which is intended to bring in, by association, right wing skepticism about the 2016 Russia investigation into Twitter’s internal decisions. However, no evidence is provided to substantiate the claim that either of these individual’s actions were politically motivated. Finally, James Baker appears to have been one of the few people at twitter with a Top Secret clearance, which would explain why he received a classified briefing. (FYI it’s also not uncommon for former FBI agents to find employment at large companies after they retire.)
In short, Schellenberger spins and selectively interprets evidence to suggest some nefarious collaboration between the FBI and Twitter, but the claim does not hold up under scrutiny. While you can question the wisdom of Twitter’s own decision to suppress the story for a short time, there is no evidence that the FBI pressured or ordered Twitter to do so.
Why Framing Matters
Zooming back, the best way to understand the Hunter Biden Laptop saga is this: Scandal 2 is essentially a temper tantrum over the fact that the attempt to create a narrative around Scandal 1 didn’t work out as planned.
I explained in a previous piece that changing the debate is a surefire way to upend a propaganda operation. By merely questioning the origins of the information provided to the New York Post, the media reframed the story. Coverage focused on vetting the source of the laptop’s contents, so the “story” became about the provenance of the emails, not their substance. It’s much easier to debate whether Hunter Biden’s business dealings were improper and insinuate wrongdoing than to explain how a blind computer repairman in Delaware and the president’s personal lawyer just happened to come into possession of the entire contents of a hard drive belonging to the troubled son of the president’s political opponent.
Obviously, Scandal 1 did not have the intended effect — and that’s exactly what those frustrated with the thwarted outcome want to prevent from happening again. The goal of Scandal 2 is to punish government and private actors for doing exactly what they should have done — double-check sources and proceed with caution when disseminating information, particularly close to an election. The goal is to reframe the story, once again.
That’s pretty much everything you need to understand Hunter Biden’s Laptop. If you’re still awake, go pour yourself another drink.













Sorry to be a broken record, but these issues again address what I mentioned during our last office hours. As Bannon said, "flood the (information) zone with s***." What tv news organization (49% said TV is 'often' their source) is going to provide this kind of depth? How many Americans will have the time desire and inclination to invest so much energy in getting to the bottom of such issues - we have 'grocery lists' to write. ;-) Sound bytes in conjunction with confirmation bias and an individual's residence in a chosen, closed media ecosystem provide an individual with the easier, simpler answer of us vs them. Sorry to be so negative, so I'll end with hope. Retired from teaching last year, but was impressed by the steps we'd taken in the Social Studies to help our high school students understand the nefarious ways of social media platforms and news organizations using tools from organizations like the Stanford Education History Group and UofWA's Social Media and the Classroom program. Asha, thanks so much for the clearly enunciated 3-step formula for dealing with such conspiracy theories. Will definitely pass on to my former colleagues as another tool for their tool kit.
We always encouraged our students to become lifelong learners, and I want to thank Asha and the rest of you for helping me to practice what I preached. Still. Love. Learning.
Thanks for the comprehensive summary. Unfortunately, the nuance, the backdrop, the innocuous motives, will be lost on MAGA nation, Fox, and the Disinformation Industrial Complex. See eg how the GOP argues that Pelosi is responsible for the J6 insurrection; see Biden’s 10 classified docs found @ UPenn office is equivalent to MAL, per the GOP.